Articles
Answering the Big Question: How to Spend on Cybersecurity?
- By Bryan Lapidus, FPAC
- Published: 12/16/2021

Cyber risk is a very real and tangible problem, and so is the question of how to spend on cybersecurity. In the 2021 AFP Risk Survey the number one risk, and hardest to manage, was cyber risk — more than the talent shortage, more than trying to figure out stalled supply chains, more than anything else. So, what do we do?
In a recent webinar with Franklin Donahoe, CEO of Lynx Technology Partners, titled “How to Spend on Cybersecurity,” Donahoe helped us understand how to assign value to our information assets and to think about the tools we might want to use in order to budget, as well as what we want to spend and how to make the right dollar investment in our information security.
The relationship between finance and IT
The conversations started with an audience poll describing the relationship between Finance and IT. The highest number of responses indicated a tight, partnership relationship between the groups, but still that implies two thirds did not attain that level.
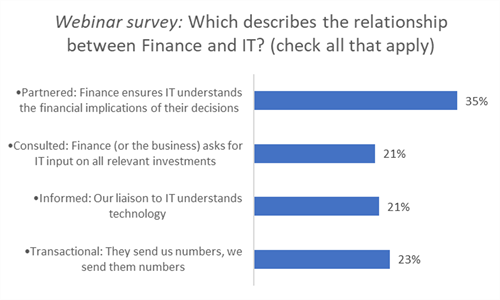
The relationship matters because information security is a business decision. From a technical role to a business-facing role, the chief information officer needs to understand the operational requirements and the application of IT and solutions to help the business, while the CISO (chief information security officer) needs to understand what the business is doing and how to protect the assets. A lot of that is translating between the security side—vulnerabilities and techno speak of security solutions—to the business it affects.
“A lot of security folks and IT folks are in love with technology and the dark science of security,” said Donahoe. “But we’re working in the business as a service organization, and so we need to understand the business. We shouldn't be spending more dollars or putting more effort into areas or technologies that have nothing to do with business value, and that is the challenge.”
“I'm really big into partnering with other service organizations that support the business to find out different aspects or angles to understand what the business means to them from a finance perspective, from an HR perspective, et cetera,” said Donahoe.
This means that Security needs to communicate with the business and have leaders in this area who can articulate and understand the business. They also need to be able to speak to business and other service organizations, such as finance, legal, IT and HR, to understand different aspects of the business.
Finding good references for your business forecast is a challenge, so AFP is pleased to bring you additional resources and data to support your planning. Visit the AFP 2022 Planning center here.
Businesses are in business to make money, put security in the same light make a return on security investment calculation: How much protection is the right level of protection, and are we spending too much or too little? If we lose too much money, if an asset is compromised or information is leaked, or ransomware prevents us from executing a specific business process, then we need to understand the cost to protect that asset.
There is a reciprocal relationship that should happen where each business leader or service partner should ask security the “what” questions: What impact does that have on the business? What is it really protecting? What risk are we avoiding? What is the business benefit? These questions assist in decision-making and securing the required funding, and form the basis of security valuation.
How cyber investments are valued
Next, the conversation moved to the central topic, allocation of spend. This survey of respondents shows the challenge in using standard valuation techniques for defensive, non-revenue producing investment by thinking of them as strategic investments or simply analyzing the knowing cost expenditures.
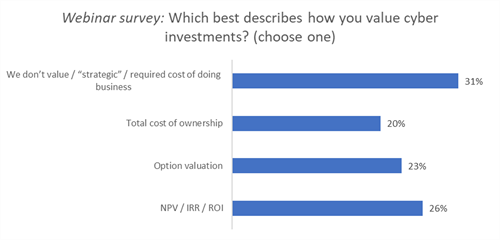
Budgets reflect needs and priorities; we spend money on things that are important to us, e.g., personnel, a certain business unit, technology. When valuing cyber investments, Donahoe advises that you gather as much information about past events, the industry and different attacks. He also advises researching what the threat actors are to your business in your industry, so you understand their techniques and how sophisticated they are. There are three basic elements to consider:
• IMPACT: But when you talk about ROI, understand that security leaders need a lot of information such as the value of assets. What are you trying to protect? What is the value that you're seeing as they're spending? Is it revenue protection, remediation costs? Brand damage or regulatory penalties?
• LIKELIHOOD: You need to understand the possible or probable number of events you're going to have in a particular category. That takes some intelligence, information-gathering and understanding. There are also some guesses that need to be made about what you're protecting or avoiding, the adverse impact on a business process, and the value of what you're protecting. This is a business discussion, not a technology discussion.
• CONTROLS: This is where the money is spent…the mechanisms of preventing, minimizing or remediating the impact and likelihood. In CISO-speak, this is the security stack.
Minimize your security costs by examining what you already have
Companies often have excess and underutilized protection for two reasons: there may be multiple technologies doing the same thing, or businesses may be using only a fraction of the capabilities available.
It’s important to ask IT and security what technologies have been applied in the last X number of years that are sitting dormant because sometimes they're not in the same organizational unit. "When IT is purchasing something, does it have security functionality that's in that bundle you're buying, or in that technology you're buying?" said Donahoe.
Some bundled technologies are actually better than the solution you purchased for that point solution. This is an opportunity to rationalize the technology stack and leverage some vendors, especially in global organizations. For example, you might be using X technology in North America, but it's being procured elsewhere and at a different price point.
“I used to tell my teams, ‘We start with eating what's in the refrigerator,’” he said. Look at the protection framework, the control framework, and all the technologies that are applied to provide security within that framework. Your vendors will tell you what’s turned on and what’s not, “because they want to sell you the whole suite of things,” said Donahoe. “They’ll tell you before your folks will tell you, and they know. Then you look at the overlap. You look at what's not being used and say, ‘I'm going to use this or I'm not,’ and it's a part of vendor management, too.”
Developing the information security budget
When it comes to developing a budget for information security, the line-by-line review of the requested spend is Donahoe’s least favorite, but was most preferred by the attendees. “It's not the way I approach security, and I think this is the disconnect. More and more security leaders, as they start to become better business partners, are going to be speaking in terms that align with the valuation of business assets. They're adding business value or they're protecting a business asset. Help them approach it in that way.”
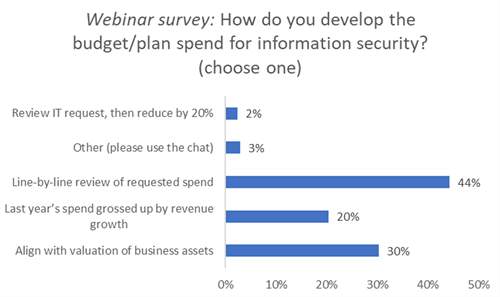
There are different tools you can use to make the right investment and set the right budgets. One is business impact analysis (BIA), which lists the data, risk profile and application of technology that is important to the business. These three elements then allow a measurement of materiality and the key question: If this particular process or asset were offline for X number of hours, how much would that cost us? [Pro-tip: materiality is an opening for finance to enter the discussion.]
Another tool is the data and application classification, which should be table stakes within a security organization. Where there's data, there's applications. Data flows through applications. Start with the data that the business uses, and that includes finance. There's financial data and credit card data. There's all different data types or information types, as well as categories to put them in, such as critical, high, moderate, and low.
“Finance should proactively be asking their CSO or senior security folks how they’re applying these decisions to them. They might be surprised you’re asking them that, but when it comes to the business value decision, this is where they should be at least starting to make those decisions,” said Donahoe.
What we can do now
“Approach security investment as an investment, not a cost,” said Donahoe. He advised finance professionals to talk to their security team about their business-centric approach — and make sure they have one. Key questions to ask include:
– What does it mean to the business?
– When you add X person to your team, what is that going to add to our business value?
– Tell me about the BIA, the data classification and application classification, and explain it in layman’s terms, not techno speak.
– Why is this technology better than that one — in terms of business impact, the availability of assets and the classification of assets?
“We're communicating technology when we should be communicating business risk,” he said. What it all comes down to is this: What impact will this have on the business?
Listen to the “How to Spend on Cybersecurity” webinar in its entirety to get the full benefit of Franklin Donahoe’s expertise.
PARTNER CONTENT
Copyright © 2024 Association for Financial Professionals, Inc.
All rights reserved.

.tmb-small.png?sfvrsn=3731146b_1)
